The talk of data protection, data breaches, and cyber security won't be going away anytime soon. As a rising threat all over the world, it's become more important than ever before to gain a deeper understanding of these trends and the short and long-term effects they could have on your business.
In the last five years, there has been a substantial increase of high-profile hacks and data breaches. But lately these cyber attacks are happening a lot more frequently and having more devastating impacts on businesses and institutions in Canada too. You must have heard about the a Canadian hospital shut down due to a ransomware attack, and also the U.S. presidential race suffering from a number of political hacks — it seems no one is immune anymore.
Another important aspect to include in your plans is managing those who have access to data and avoid situations where internal hacks can access data they should not have rights to. By developing a coherent data management strategy to organize, govern, analyze and deploy your company’s data assets, you will help keep it protected and safe.
Perimeter security used to be an area companies focused on vs endpoint protection, data-centric security and data loss prevention. With mobility on the rise and security perimeters expanding at an unprecedented rate, companies now need to find solutions that keep data secure from inside the network and from external threats. This has changed the whole data protection landscape and keeps experts sharing knowledge and thought leadership. Vendors now offer new approaches and new technologies to address today’s requirements.
In order to stay ahead of the curve, it's important to stay informed. Check out a recent Storage Evaluation Guide from the Evaluator Group. It presents technologies and corresponding use cases that help shed some light in a more effective way than looking at marketing materials from manufacturers.
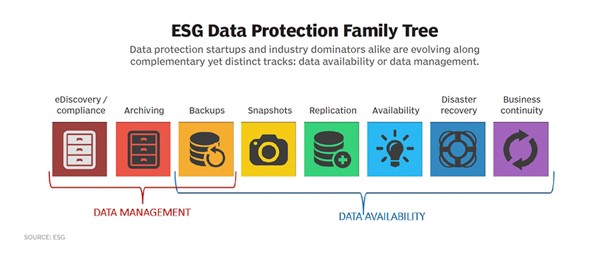
This graph from ESG is also a good depiction of the different components involved in a strong and effective data management strategy.
As a starting point:
1. Evaluate your current data protection set-up, and find out if you have any gaps
2. Map out your business requirements and evaluate the data protection approaches that align with your objectives
3. Review and analyze new solutions and see how they can help address your needs
4. Take our short quiz to get a high-level snapshot of your current situation and then we can start a conversation.
Sentia’s core expertise is data protection and data storage solutions. We can help position your business to stay ahead of the curve and ensure your assets are protected and your team is armed with the knowledge they need. Feel free to contact me to keep the conversation going.
Paul Oh
CTO
Sentia